Download free brush illustrator
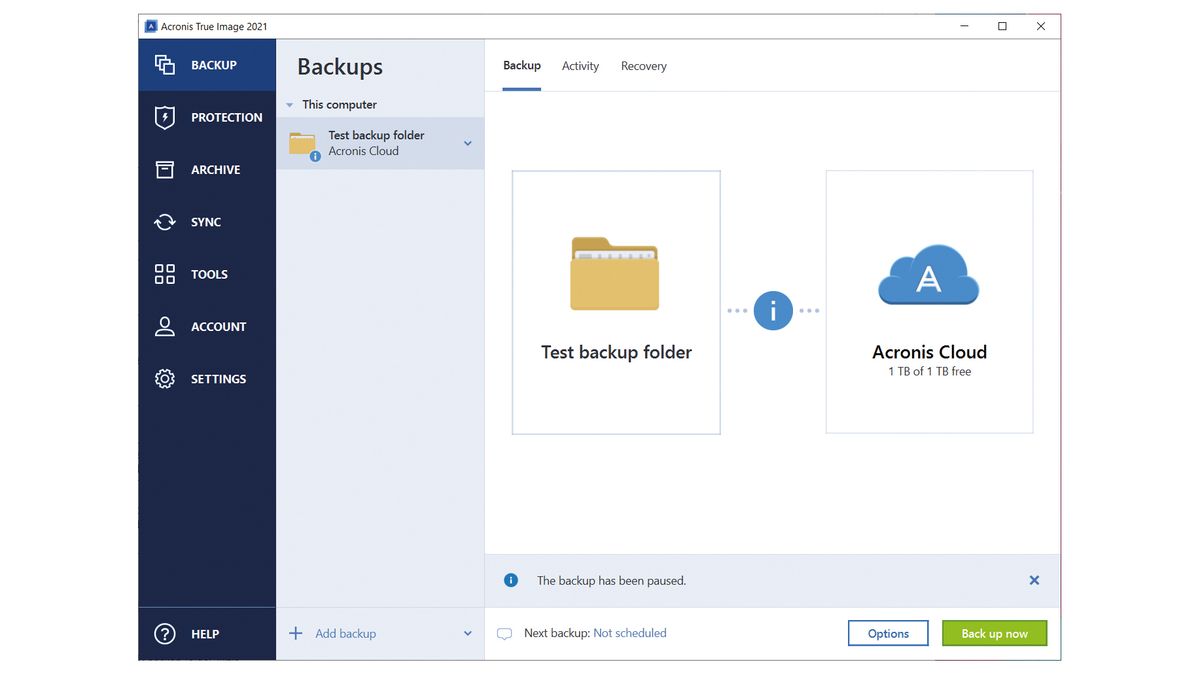
Acronis True Image Premium 5.
acrobat reader 11 latest version free download
| Adobe illustrator lite portable download | Adobe acrobat pro trial full download |
| Acronis true image business use | Pte3 |
| Visualboy advance | Pokemon quest china |
| House party the game mobile | 347 |
| Acronis true image business use | 256 |
| Bleach the third phantom rom | Acronis true image 2015 windows 10 |
| Custom shapes for photoshop cs5 free download | Vulnerability assessments: Acronis True Image includes vulnerability assessments that scan your system for potential security weaknesses and provide recommendations for improvement. Granularly control the access to websites based on 44 categories. Protecting your data is more important than ever. Active Protection. Actively protect all the data on your systems from ransomware and automatically roll back any changes made to your system with Acronis Active Protection. ASign - allows electronic signatures to be added to a document. Security Updates. |
| Illustrator to pdf converter free download | 91 |
| Myracehorse coupon code | Cloud backup. Active Protection. Acronis True Image Subscription Advanced. Regularly check for updates and install them promptly to benefit from the latest security enhancements and bug fixes. Supported platforms. |
| Adobe illustrator cs5 me torrent download | The software actively monitors your system for various threats, such as malware, ransomware, and suspicious activities, in real time. Acronis Cloud Manager provides advanced monitoring, management, migration, and recovery for Microsoft Cloud environments of all shapes and sizes, including single and multi-tenant public, private, and hybrid cloud configurations. Provision multiple systems with just a click, and manage everything � from backup policies to vulnerability assessments and patching � through a single pane of glass. Getting started with Acronis' cyber protection solutions is simple and painless. Refer to this page to check if you can get a free upgrade. Local backups � to internal or external drives or network share. Continuous data protection. |
Share: